Implementation Guide-1
“The world breaks everyone, and afterward, some are strong at the broken places.”
Physical Device and System Inventory
This guide provides an actionable approach to implementing NIST ID.AM-1: "Physical devices and systems within the organization are inventoried." It outlines specific steps and best practices for organizations to effectively inventory their physical devices and systems.
1. Establish Inventory Scope and Objectives
Define what constitutes a "physical device" and "system" for your organization. This may include:
Servers, workstations, and laptops
Network devices (routers, switches, firewalls)
Mobile devices (smartphones, tablets)
IoT devices, Industrial control systems
Printers and multifunction devices
2. Select and Implement Inventory Tools
Actions:
Choose appropriate inventory management tools. Options include:
Enterprise-grade solutions: ServiceNow, BMC Atrium CMDB, or Microsoft System Center Configuration Manager (SCCM)
Open-source alternatives: OCS Inventory, Snipe-IT, or Ralph
Implement automated discovery tools to support the inventory process:
Network scanning tools: Nmap, Angry IP Scanner, or Advanced IP Scanner
Asset discovery solutions: Lansweeper, Spiceworks, or SolarWinds Network Topology Mapper
Configure tools to collect required information automatically where possible.
Set up regular automated scans (e.g., weekly) to keep the inventory up-to-date.
3. Conduct Initial Inventory
Perform a comprehensive initial scan using the chosen automated tools.
Conduct a physical walk-through of all facilities to identify devices that may not be network-connected.
Review procurement records and asset registers to cross-reference and identify any missing items.
For each device/system, record:
Unique identifier (e.g., asset tag, serial number)
Type of device/system
Make and model
Operating system and version (if applicable)
Physical location
Responsible owner/department
Purpose/function
Network information (IP address, MAC address)
Purchase date and expected end-of-life
Establish a process for manually adding devices that can't be automatically discovered.
4. Implement Ongoing Inventory Maintenance Processes
Actions:
Establish clear procedures for:
Adding new devices/systems to the inventory
Updating information for existing inventory items
Removing decommissioned devices/systems
Integrate the inventory process with:
Procurement procedures to capture new acquisitions
Change management processes to track system changes
Decommissioning procedures to ensure timely removal
Assign responsibility for inventory maintenance to specific roles or teams.
Set up automated alerts for new device discoveries or changes to critical systems.
Implement a regular reconciliation process (e.g., monthly) to verify inventory accuracy.
5. Establish Access Controls and Monitoring
Implement role-based access controls for the inventory system, set up logging and auditing for all changes to the inventory.
6. Conduct Regular Audits and Validation
Regularly review access logs and change history (e.g., quarterly), and implement monitoring to detect unauthorized devices on the network:
Configure network access control (NAC) solutions to alert on unknown devices
Use network behavior anomaly detection (NBAD) tools to identify unusual device activity
Perform quarterly physical audits of a sample of inventory items to verify accuracy.
Conduct an annual comprehensive inventory review, including physical verification of all items.
Compare inventory data with other sources (e.g., network scans, procurement records) to identify discrepancies.
Document and investigate any discrepancies found during audits.
Update inventory procedures based on audit findings to improve accuracy and completeness.
7. Reporting and Metrics
Actions:
Develop key performance indicators (KPIs) for the inventory process, such as:
Inventory coverage (% of devices accounted for)
Inventory accuracy (% of entries verified as correct)
Average time to add new devices to inventory
Generate monthly reports on inventory status and KPIs.
Provide dashboard views for management to easily assess the current state of the inventory.
Use inventory data to support other security processes (e.g., vulnerability management, incident response).
8. Training and Awareness
Actions:
Develop training materials on inventory procedures for relevant staff.
Conduct annual training sessions for personnel involved in inventory management.
Include inventory management responsibilities in relevant job descriptions and performance evaluations.
Create and distribute quick reference guides for common inventory tasks.
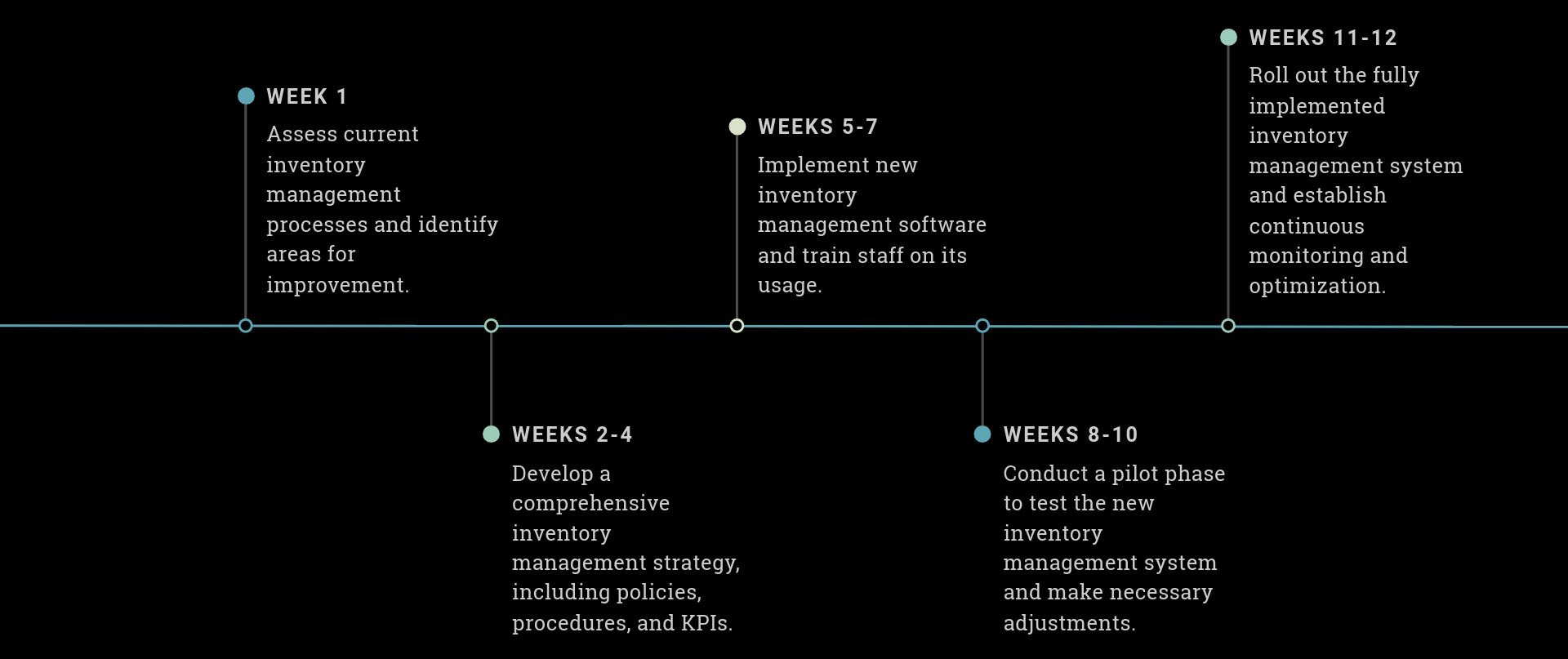
Implementation Strategy
Plan and Prepare (Weeks 1-2):
Define scope and objectives
Select and procure necessary tools
Develop initial procedures and policies
Initial Implementation (Weeks 3-6):
Deploy inventory and discovery tools
Conduct initial comprehensive inventory
Set up automated processes and integrations
Process Refinement (Weeks 7-10):
Establish ongoing maintenance procedures
Implement access controls and monitoring
Develop reporting and metrics
Validation and Training (Weeks 11-12):
Conduct initial audit to validate inventory
Deliver training to relevant personnel
Make necessary adjustments based on initial findings
Ongoing Operations:
Regular maintenance and updates
Quarterly sample audits
Annual comprehensive review and validation